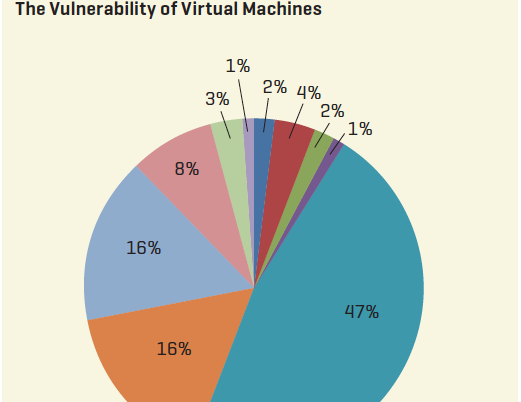
SECTION: Features
Cybersecurity involves protection of computer systems from theft, damage, or manipulation to the hardware, software, or the data contained on them. A limitless cyberspace, little to no boundaries, and eroding national borders is making Africa vulnerable to cyber threats and potential harms. Cybersecurity represents serious economic and national security challenges, which need to be properly defined and contextualized.
By Hood Mukiibi, November 2019
PDF | HTML | In the Digital Library

Dan Keyserling, head of communications at Jigsaw, an incubator within Alphabet, shares how technology can help address global challenges, especially on the front lines of press freedom, political repression, and human rights.
By Nidhi Rastogi, April 2017
PDF | HTML | In the Digital Library

SECTION: Features
Cyberspace, a world of great promise, but also, of great peril. Pirates, predators, and hackers galore, are you and your online identity at risk in this wild frontier?
By Jason R. C. Nurse, March 2015
PDF | HTML | In the Digital Library

The lives and times of the British women who operated Colossus, and their all-important role in events leading to D-Day and the close of the Second World War.
By Michael Smith, March 2015
PDF | HTML | In the Digital Library

DEPARTMENT: Blogs
The XRDS blog highlights a range of topics from security and privacy to neuroscience. Selected blog posts, edited for print, will be featured in every issue. Please visit xrds.acm.org/blog to read each post in its entirety. Keeping with our theme of professional development, included is a guest post on how to craft a publishable research paper.
By Dimitris Mitropoulos, December 2013
PDF | HTML | In the Digital Library

SECTION: Features
Protecting data privacy and anonymity requires a better understanding of the conditions and mechanisms under which they may be threatened.
By Elaine Mackey, Mark Elliot, September 2013
PDF | HTML | In the Digital Library

DEPARTMENT: Labz
CUPS, a research lab at Carnegie Mellon University, is dedicated to addressing the broad array of challenges collectively called "usable privacy and security."
By Rich Shay, September 2013
PDF | HTML | In the Digital Library

The newly launched XRDS blog highlights a range of topics from conference overviews to privacy and security, from HCI to cryptography. Selected blog posts, edited for print, will be featured in every issue. Please visit xrds.acm.org/blog to read each post in its entirety.
By Wolfgang Richter, Dimitris Mitropoulos, December 2012
PDF | HTML | In the Digital Library
By observing how covert financial networks operate in online games like World of Warcraft, we can learn about how they might function offline.
By Brian Keegan, Muhammad Aurangzeb Ahmad, Dmitri Williams, Jaideep Srivastava, Noshir Contractor, March 2011
PDF | HTML | In the Digital Library
Suspicious network patterns may be the key to detecting criminals and fraudsters on e-commerce sites.
By Polo Chau, March 2011
PDF | HTML | In the Digital Library

The CIO of USAA, a full-service, branchless financial services operation, sees much more to banking than e-transactions.
By James Stanier, March 2011
PDF | HTML | In the Digital Library

Cloud computing is a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources that can be rapidly provisioned and released with minimal management effort or service provider interaction. With this pay-as-you-go model of computing, cloud solutions are seen as having the potential to both dramatically reduce costs and increase the rapidity of development of applications.
By Ramaswamy Chandramouli, Peter Mell, March 2010
PDF | HTML | In the Digital Library

Research related to online social networks has addressed a number of important problems related to the storage, retrieval, and management of social network data. However, privacy concerns stemming from the use of social networks, or the dissemination of social network data, have largely been ignored. And with more than 250 million active Facebook (http://facebook.com) users, nearly half of whom log in at least once per day [5], these concerns can't remain unaddressed for long.
By Grigorios Loukides, Aris Gkoulalas-Divanis, December 2009
PDF | HTML | In the Digital Library
Computer attacks are now commonplace. By connecting your computer to the Internet, you increase the risk of having someone break in, install malicious programs and tools on it, and possibly use it to attack other machines on the Internet by controlling it remotely.Several major banks have been subject to attacks, in which attackers gained access into customers' accounts and viewed detailed information about the activities on these accounts. In some instances the attackers stole credit card information to blackmail e-commerce companies by threatening to sell this information to unauthorized entities. Several online trading companies and e-commerce sites were shut down temporarily due to major packet flood attacks, also known as Denial-of-Service (DoS) attacks, causing these companies to lose revenue, customer satisfaction, and trust [10]. A major software development company discovered that attackers had broken into its network and stolen the source code for future releases of its popular products. Just recently, the source code of the future flagship product belonging to a major software development company was stolen and made publicly available on the Internet.In order to combat this growing trend of computer attacks, both academic and industry groups have been developing systems to monitor networks and systems and raise alarms of suspicious activities. These systems are called Intrusion Detection Systems (IDS).
By Khaled Labib, September 2004
PDF | HTML | In the Digital Library
The explosive growth of networked and internetworked computer systems during the past decade has brought about a need for increased protection mechanisms. This paper discusses three authentication protocols that incorporate the use of methods that present effective user authentication. The first two protocols have been previously discussed in the literature; the third protocol draws from the first two and others to produce an authentication scheme that provides both mutual authentication and secure key distribution which is easy to use, is compatible with present operating systems, is transparent across systems, and provides password file protection.
By Charles Cavaiani, Jim Alves-Foss, April 1996
PDF | HTML | In the Digital Library