SECTION: Features
Organizers at the intersection of anticolonial justice and technology, Gabriel Schubiner and Mallika G. Dharmaraj discuss their journeys, the historical context of their work, and organizing strategies.
By Gabriel Schubiner, Mallika G. Dharmaraj, June 2024
PDF | HTML | In the Digital Library
In a revolt against techno-optimism and the real-world violence it upholds, members of radical research collective Lucy Parsons Labs (LPL) call for an empiricism rooted in technopolitical critique. Drawing from their own years of labor in the struggles against racial and surveillance capitalism, current work in HCI, and radical theorists like Alfredo M. Bonanano and Modibo Kadalie, LPL invites us to incorporate an ethics of rebellion and progress our tech practices into principled, anti-authoritarian praxis.
By Alejandro Ruizesparza, Freddy Martinez, June 2024
PDF | HTML | In the Digital Library
SECTION: Features
Big tech companies have been found to misuse personal data, often collected without consent. What can the public do to change unjust collection and use of their personal data, and what role can computer scientists play in these efforts?
By Jonathan Zong, December 2020
PDF | HTML | In the Digital Library

Cybersecurity involves protection of computer systems from theft, damage, or manipulation to the hardware, software, or the data contained on them. A limitless cyberspace, little to no boundaries, and eroding national borders is making Africa vulnerable to cyber threats and potential harms. Cybersecurity represents serious economic and national security challenges, which need to be properly defined and contextualized.
By Hood Mukiibi, November 2019
PDF | HTML | In the Digital Library

SECTION: Features
How can we promote an internet that respects human rights? Investing in autonomous infrastructure built and operated by politically motivated techies, who put their skills at the service of the public interest, may be the answer.
By Stefania Milan, July 2018
PDF | HTML | In the Digital Library

This article discusses the consequences of the commercialization and evolution of the Internet infrastructure, and how it affects our ability to exercise human rights online.
By Niels ten Oever, Davide Beraldo, July 2018
PDF | HTML | In the Digital Library

SECTION: Features
The use of unmanned aerial drones will revolutionize news reporting, but many issues need to be resolved before things can really take off.
By Matt Waite, March 2014
PDF | HTML | In the Digital Library

DEPARTMENT: Blogs
Stanford grad student Jonathan Mayer discusses cookies, Web tracking, and changes to Mozilla's cookie policy.
By Jonathan Mayer, September 2013
PDF | HTML | In the Digital Library

SECTION: Features
Revealing private content on the Web can also spark public engagement. To understand this, we need to challenge our common sense notions of privacy and democracy.
By Andreas Birkbak, September 2013
PDF | HTML | In the Digital Library
The line between personal and anonymous information is often unclear. Increasingly it falls to lawyers to understand and manage the risks associated with the sharing of "anonymized" data sets.
By Marion Oswald, September 2013
PDF | HTML | In the Digital Library

Why defining what counts as personal data is important for data protection and information sharing.
By Iain Bourne, September 2013
PDF | HTML | In the Digital Library

People think they want anonymity, but actually desire privacy. But how do we reframe the debate surrounding privacy and security? Perhaps technology is the answer.
By David Birch, September 2013
PDF | HTML | In the Digital Library

The vast amounts of data that are now available provide new opportunities to social science researchers, but also raise huge privacy concerns for data subjects. Differential privacy offers a way to balance the needs of both parties. But how?
By Christine Task, September 2013
PDF | HTML | In the Digital Library

Distinguished Scientist at Microsoft Research, Dr. Cynthia Dwork, provides a first-hand look at the basics of differential privacy.
By Michael Zuba, September 2013
PDF | HTML | In the Digital Library

In this profile, Jessica Staddon discusses managing privacy research for one the world's best-known technology corporations.
By Adrian Scoică, September 2013
PDF | HTML | In the Digital Library

DEPARTMENT: Labz
CUPS, a research lab at Carnegie Mellon University, is dedicated to addressing the broad array of challenges collectively called "usable privacy and security."
By Rich Shay, September 2013
PDF | HTML | In the Digital Library
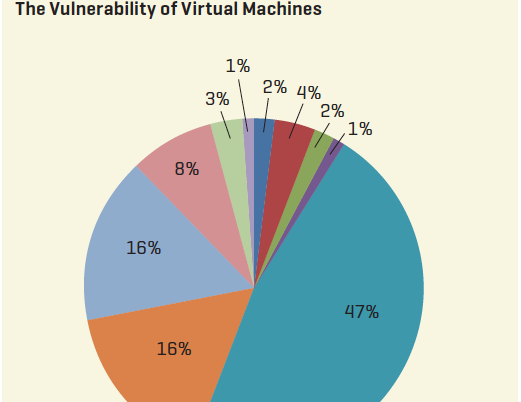
In this paper, a secure environment for electronic commerce is introduced. The environment is formed via a synthesis of biometrics consumer authentication with a security token. Such a token is a smart card containing cryptographic keys and a cryptographic microprocessor for data encryption. The keys are used to further authenticate the possessor of the card as the actual owner and also to facilitate secure electronic financial transactions. New technologies like these bring benefits to society by enhancing the standard of living, however, numerous challenges are introduced [1].Biometrics is a Greek composite word stemming from the synthesis of bio and metric, meaning life measurement. In this context, the science of biometrics is concerned with the accurate measurement of unique biological characteristics of an individual in order to securely identify them to a computer or other electronic system. Biological characteristics measured usually include fingerprints, voice patterns, retinal and iris scans, face patterns, and even the chemical composition of an individual's DNA [9].
By Sofia Gleni, Panagiotis Petratos, September 2004
PDF | HTML | In the Digital Library